Configuring Okta
Note: These instructions pertain to Step 2 of the overall identity provider process.
To configure Okta as your identity provider for Prysm, you need to complete the two sets of interrelated steps below.
Follow these steps:
- Sign in to Okta as an administrator (https://www.okta.com/login/).
- Select Applications.
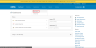
- Click Add Applications.
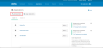
- Click the Create New App button.
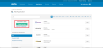
- In the Platform field, select Web.
- In the Sign on method field, select SAML 2.0, and click Create.
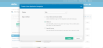
- In the General Settings section, in the App name field, enter the name that the customer uses for the Prysm application, and click Next.

- In the SAML Settings section, in the Single sign on URL field, enter the string from the Callback URL field in Prysm Admin Portal. (See Step 6 of your Prysm configuration.)
- In the Audience URI (SP Entity ID) field, enter app.prysm.com. (See Step 7 of your Prysm configuration.)
This is the unique identifier for the customer's Prysm application. Tip: You can leave the Default RelayState, Name ID Format, and Application Username fields blank, because they aren't needed for integration with Prysm.
Tip: You can leave the Default RelayState, Name ID Format, and Application Username fields blank, because they aren't needed for integration with Prysm. - In the Attribute Statements section, map the following items in the Name field to the following Values. (These fields are required when auto provisioning is enabled.)
FirstName to user.firstName
LastName to user.lastName
EmailAddress to user.email Tip: If any attributes listed here are not in Okta, add them.
Tip: If any attributes listed here are not in Okta, add them. - In the Group Attribute Statements section, map the following item in the Name field to the following Attribute. (This field is required for role mapping in Prysm.)
Groups to list of Prysm groups - Click Next.
- In the Are you a customer or partner? field, click I'm an Okta customer adding an internal app.
- Click Finish.
- On the Settings page, click Identity Provider metadata to download the metadata file.
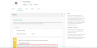
- On the Settings page, also click the View Setup Instructions button.
You see a page with fields of information, such as Identity Provider Issuer, which you need as you configure Prysm to work with Okta.
Follow these steps:
- Impersonate the account you want to configure.
- In Admin Portal, click Identity Provider.

- On the Identity Providers page, set the Enable SSO toggle to On.
- In the Identity Provider field, select Okta.
When you select Okta, the Protocol field is automatically set to SAML 2.0. - In the Auto Provisioning field, set the toggle to On or Off.
On: When Auto Provisioning is On, users who attempt to sign in to Prysm for the first time see the Okta sign in page. When they sign in to Okta, Prysm automatically creates that user in Prysm.
Off: When Auto Provisioning is Off, a Prysm administrator must create a user record for each user before that user signs into Prysm for the first time. Then, when the user attempts to sign in to Prysm, she enters her Okta sign in information and is able to access Prysm.Note: If you turn on Auto Provisioning, contact Prysm support at support@prysm.com. Prysm support must add your domain to a whitelist. - In the Callback URL field, verify that the URL matches the URL you entered in the Single sign on URL field in Step 8 of your Okta configuration.
- In the SPID field, enter app.prysm.com. (See Step 9 of your Okta configuration.)
- In the Attach SAML Request field, set the toggle to On or Off. Prysm supports On or Off. If you don't know which one to use, contact your IT department to determine whether your specific SAML configuration requires the SAML request to be attached.
On: When Attach SAML Request is On, the request to redirect to Okta's sign in page is attached.
Off: When Attach SAML Request is Off, the request to redirect to Okta's sign in page is not attached. - In the Entry Point field, enter the URL of the Okta sign in page.
You can find this URL in the Identity Provider Single Sign On URL field, after you click View Setup Instructions in Step 16 of your Okta configuration. - In the Certificate field, enter the encoded SSO certificate.
You can find this in the X.509 Certificate field, after you click View Setup Instructions in Step 16 of your Okta configuration. - In the Issuer field, enter the Okta issuer string.
You can find this string in the Identity Provider Issuer field, after you click View Setup Instructions in Step 16 of your Okta configuration. - In the Org_Admin field, enter the group ID for Org Admins that you mapped in Step 11 of your Okta configuration.
- In the Basic_User field, enter the group ID for Basic Users that you mapped in Step 11 of your Okta configuration.
- If the Auto-Provisioning toggle is set to On, the PAS User Field Name field is automatically set to IdP Attribute Name when a user is auto-provisioned.
- In the First Name and Last Name fields, enter the values that you mapped in Step 10 of your Okta configuration.
- In the Groups field, enter any other groups that are mapped to users (see Step 11 of your Okta configuration).
For more information, see Associating Prysm permission groups and identity provider groups.Warning: Role mapping must be configured for at least one group. - In the Enforce SSO field, set the toggle to On or Off.
On: When Enforce SSO is On, users can sign in only one way — with their Okta credentials.
Off: When Enforce SSO is Off, users can sign in two ways — with their Okta credentials or with their Prysm credentials.Warning: Before you change this setting and click Save in the next step, be sure to test your IdP configuration with at least one user. If you click Save to convert all your users to IdP authentication without testing, and something in your configuration is not correct, you can lock all users out of their accounts. - Click Save.
- To ensure a successful identity provider integration, move on to Step 3 and complete the entire Process for Configuring Identity Providers.