Configuring G Suite
Note: These instructions pertain to Step 2 of the overall identity provider process.
To configure G Suite as your identity provider for Prysm, you need to complete the two sets of interrelated steps below.
Follow these steps:
- Navigate to the Google API Console (https://console.developers.google.com/projectselector/apis/library?pli=1).
- In the project list, select your project.
If you haven’t created a project, create one by clicking Create a new project.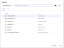
- In the left panel, click Credentials, and then click the OAuth consent screen tab.
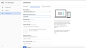 Tip: You can leave the Optional fields blank, because they aren't needed for integration with Prysm.
Tip: You can leave the Optional fields blank, because they aren't needed for integration with Prysm. - Complete the fields on the OAuth consent screen tab.
- Click Save.
- Click the Credentials tab.
- Click Create credentials > OAuth client ID.
- Under Application type, select Web application.
- In the Name field, enter the name of the service provider.
- In the Authorized redirect URIs field, enter the string from the Callback URL field in Prysm Admin Portal. (See Step 6 of your Prysm configuration.)
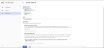
- Click Create.
The OAuth Client dialog box appears. - Copy the Client ID and the Client Secret. Keep them for Steps 7 and 8 of your Prysm configuration.
Follow these steps:
- Impersonate the account you want to configure.
- In Admin Portal, click Identity Provider.
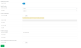
- On the Identity Providers page, set the Enable SSO toggle to On.
- In the Identity Provider field, select G Suite.
When you select G Suite, the Protocol field is automatically set to OAuth 2.0. - In the Auto Provisioning field, set the toggle to Off.
Warning: Currently, Auto Provisioning must be Off for G Suite integrations, because G Suite does not support role mapping.
- In the Callback URL field, verify that the URL matches the URL you entered in the Authorized Redirect URIs field in Step 10 of your G Suite configuration.
- In the Client ID field, enter the ID that you copied from the Client ID field in G Suite’s settings (see Step 12 of your G Suite configuration).
- In the Client Secret field, enter the text that you copied from the Client Secret field in G Suite’s settings (see Step 12 of your G Suite configuration).
- In the Scope field, enter the Google APIs that retrieve the user’s profile and email (separated by a comma). For example:
https://www.googleapis.com/auth/userinfo.profile, https://www.googleapis.com/auth/userinfo.email - If the Auto-Provisioning toggle is set to On, the PAS User Field Name field is automatically set to IdP Attribute Name when a user is auto-provisioned.
Also, the First Name and Last Name fields are set to the parameters that contain a user’s first name and last name. - In the Enforce SSO field, set the toggle to On or Off.
On: When Enforce SSO is On, users can sign in only one way — with their G Suite credentials.
Off: When Enforce SSO is Off, users can sign in two ways — with their G Suite credentials or with their Prysm credentials.Warning: Before you change this setting and click Save in the next step, be sure to test your IdP configuration with at least one user. If you click Save to convert all your users to IdP authentication without testing, and something in your configuration is not correct, you can lock all users out of their accounts. - Click Save.
- To ensure a successful identity provider integration, move on to Step 3 and complete the entire Process for Configuring Identity Providers.