Configuring Active Directory Federation Services
Note: These instructions pertain to Step 2 of the overall identity provider process.
To configure Active Directory Federation Services (ADFS) as your identity provider for Prysm, you need to complete the two sets of interrelated steps below.
Follow these steps:
- Open Microsoft Windows Server 2012 (or 2012 R2).
- Sign in to your ADFS account.
- Open Server Manager.

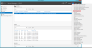
- Click Tools > ADFS Management.
-
In the Actions panel, click Add Relying Party Trust.
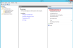
The Add Relying Party Trust Wizard window opens. - In the Add Relying Trust Wizard window, click Next to move past the Welcome step.
- On the Select Data Source step, select Enter data about the relying party manually, and click Next.
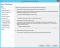
- On the Specify Display Name step, enter prysmsso (or any display name you prefer), and click Next.

- On the Choose Profile step, select ADFS profile, and click Next.
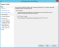
- On the Configure Certificate step (which is optional), if you want to use an SSL token encryption certificate, click Browse, select the certificate, and click Next.
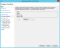
- On the Configure URL step, check the box for Enable support for the SAML 2.0 WebSSO protocol.
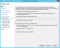
- In the Relying party SAML 2.0 SSO service URL field, enter the string from the Callback URL field in Prysm Admin Portal. (See Step 5 of your Prysm configuration.) Then click Next.
- On the Configure Identifiers step, in the Relying party trust identifier field, enter the same value you entered in the Realm field for Step 8 of your Prysm configuration. Then click Add, and click Next.
Tip: You create your own identifier / realm, using this format: PrysmSSOYourCompanyName (replace YourCompanyName with the customer's company).
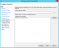
- On the Configure Multi-factor Authentication Now? step, select I do not want to configure multi-factor authentication settings for this relying trust party at this time, and click Next.
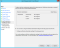
- On the Choose Issuance Authorization Rules step, select Permit all users to access this relying party, and click Next.
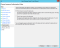
- On the Ready to Add Trust step, verify your configuration for all the steps, and click Next.
- On the Finish step, check the box for Open the Edit Claim Rules dialog for this relying party trust when the wizard closes, and click Close.
If the Add Transform Claim Rule Wizard doesn't open automatically, or you stop the process and need to open the wizard later, in the Actions panel, click Edit Claim Rules.
- In the Add Transform Claim Rule Wizard's Claim Rule Template field, select Send LDAP Attributes as Claims, and click Next.
The Edit Rule dialog box opens.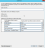
- In the Edit Rule dialog box's Mapping of LDAP attributes to outgoing claim types list, map the following LDAP Attributes to the following Outgoing Claim Types:
E-mail-Addresses to Name
Given-Name to Given Name
Surname to Surname
User-Principal-Name to E-Mail Address
Token-Groups - Unqualified Names to GroupTip: If any attributes listed here are not in ADFS, add them. Also, make sure the Attribute Store field is set to Active Directory. - Click OK.
- Download the metadata XML file at this URL (replace the italicized text with your specific domain):
https://yourdomain/FederationMetadata/2007-06/FederationMetadata.xml
Here is an example portion of a metadata XML file:
You use the metadata XML file to find information such as Identity Provider URL and Thumbprint needed for Steps 9 and 10 of your Prysm configuration.
Follow these steps:
- Impersonate the account you want to configure.
- In Admin Portal, click Identity Provider.
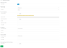
- On the Identity Providers page, set the Enable SSO toggle to On.
- In the Identity Provider field, select ADFS/Azure-AD.
When you select ADFS/Azure-AD, the Protocol field is automatically set to SAML 2.0. - In the Auto Provisioning field, set the toggle to On or Off.
On: When Auto Provisioning is On, users who attempt to sign in to Prysm for the first time see the Active Directory Federation Services sign in page. When they sign in to Active Directory Federation Services, Prysm automatically creates that user in Prysm.
Off: When Auto Provisioning is Off, a Prysm administrator must create a user record for each user before that user signs in to Prysm for the first time. Then, when the user attempts to sign in to Prysm, she enters her Active Directory Federation Services sign in information and is able to access Prysm.Note: If you turn on Auto Provisioning, contact Prysm support at support@prysm.com. Prysm support must add your domain to a whitelist. - In the Callback URL field, verify that the URL matches the URL you entered in the Relying party SAML 2.0 SSO service URL field in Step 12 of your ADFS configuration.
- In the Attach SAML Request field, set the toggle to On or Off. Prysm supports On or Off. If you don't know which one to use, contact your IT department to determine whether your specific SAML configuration requires the SAML request to be attached.
On: When Attach SAML Request is On, the request to redirect to the Active Directory Federation Services sign in page is attached.
Off: When Attach SAML Request is Off, the request to redirect to the Active Directory Federation Services sign in page is not attached. - In the Realm field, enter the relying party trust identifier from Step 13 of your ADFS configuration.
Tip: You create your own identifier/realm, using this format: PrysmSSOYourCompanyName (replace YourCompanyName with the customer's company).
- In the Identity Provider URL field, enter the URL of the Active Directory Federation Services sign in page.
This is the Location value from the node <SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect"/> in the SAML Metadata file you downloaded in Step 21 of your ADFS configuration. - To get the value for the Thumbprint field, follow these steps:
- Copy the X.509 Certificate from the metadata file you downloaded during Active Directory Federation Services configuration. (See Step 21 of your ADFS configuration. Use the certificate located in the metadata file's <KeyDescriptor use="signing"> node.)
- Go to https://www.samltool.com/fingerprint.php, which is a free thumbprint/fingerprint calculator.
- Paste the X.509 Certificate and follow the site's directions to calculate a fingerprint.
- Copy the fingerprint from the calculator, and paste it into Prysm Admin Portal's Thumbprint field.
- In the Org_Admin field, map the group ID for Org Admins from your configuration of Active Directory Federation Services. (See Step 19 of ADFS configuration.)
- In the Basic_User field, map the group ID for Basic Users from your configuration of Active Directory Federation Services. (See Step 19 of ADFS configuration.)
- If the Auto-Provisioning toggle is set to On, the PAS User Field Name field is automatically set to IdP Attribute Name when a user is auto-provisioned.
- In the First Name and Last Name fields, enter the values that you mapped in Step 19 of your ADFS configuration.
- In the Role Mapping section's PAS Group/Role Name fields, enter names for user groups you want to map. In the IdP Group Name fields, enter the unique GUID from ADFS's group details page for each group. (See Step 19 of your ADFS configuration).
Tip: The PAS Group/Role Name does not have to match the ADFS group name. However, the IdP Group Name must match the group GUID displayed in ADFS, which has the format xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx.For more information, see Associating Prysm permission groups and identity provider groups.Warning: Role mapping must be configured for at least one group.
- In the Enforce SSO field, set the toggle to On or Off.
On: When Enforce SSO is On, users can sign in only one way — with their Active Directory Federation Services credentials.
Off: When Enforce SSO is Off, users can sign in two ways — with their Active Directory Federation Services credentials or with their Prysm credentials.Warning: Before you change this setting and click Save in the next step, be sure to test your IdP configuration with at least one user. If you click Save to convert all your users to IdP authentication without testing, and something in your configuration is not correct, you can lock all users out of their accounts. - Click Save.
- To ensure a successful identity provider integration, move on to Step 3 and complete the entire Process for Configuring Identity Providers.